Journalists from German state broadcaster ARD could hardly believe their eyes when they bought used photocopiers for their research and found tax assessment notices, patient files, and even arrest warrants:
For the medical facilities, law firms, and tax advisors involved, this type of data leak can be disastrous. Under section 203 of the German Criminal Code, the disclosure of personal secrets can lead to fines or even custodial sentences.
Since the General Data Protection Regulation (GDPR) came into force across the EU in May 2018, anyone found guilty of unauthorized disclosure of personal data may face fines of up to €20 million or 4 percent of total annual worldwide turnover (Article 83 (5) GDPR) . That is why data erasure must be integrated into the data protection process.
Selecting the right erasure process
You should also consider costs when it comes to erasing your data. It makes no sense to apply the same extensive and costly full erasure method to all of your assets. Before deciding on an erasure method, you should conduct a risk assessment. The DIN 66399 standard specifies three classification levels for this purpose, and data is categorized by the level of protection it requires:
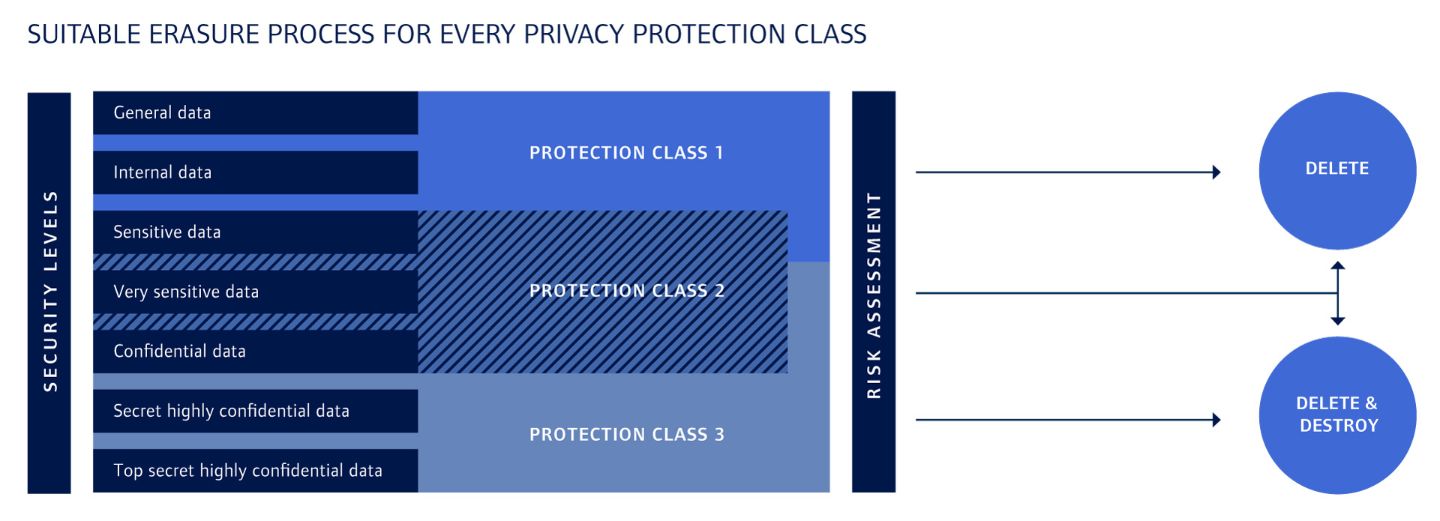
Each level is divided into several security levels which define the amount of effort required to reconstruct the data. The type of erasure method used will depend not only on how sensitive the data is but also on the media on which it is stored. Magnetic storage media, for example, require different erasure methods than flash or SSD media do.
Finding the right service provider
Data erasure that complies with the law is complex and requires expertise. And quite often, data erasure projects will fail due to a lack of resources. In most cases, the best course of action is to engage an experienced IT service provider to handle the erasure of your data. Here are some criteria to consider:
Tailor-made data erasure plan
The service provider should provide a detailed and cost-effective plan that takes the class and security level into account.
End-to-end security
Under no circumstances should data requiring a high or very high level of protection be allowed to fall into the wrong hands. Great care must therefore be taken during collection and transport, for example by using sealed containers and GPS-based monitoring of the transport route. The data erasure process should be server-based and automated, and carried out in access-restricted areas.
Full audit trail and compliant documentation
For each asset, you should receive a detailed erasure certificate containing information on the date of the erasure and the method used.
High scalability and flexibility
The service provider should be able to handle even large volumes of old assets, covering PCs, laptops, smartphones, photocopiers, printers, scanners, and other devices.
Compliance with standards
The IT service provider should comply with accepted industry standards, such as those of the Federal Office for Information Security. You should also look out for ISO-certified erasure methods.
Remarketing old IT equipment
Old equipment can be remarketed once the data on it has been successfully and properly erased, and the sale proceeds can be used toward lease costs or depreciation. This also avoids e-waste and contributes to a better environmental footprint, as does the certified recycling of systems that cannot be remarketed. The rollback and remarketing phase of IT equipment often coincides with the rollout of new systems, thus avoiding waiting periods or outages.
Before IT equipment is disposed of or remarketed, any data it contains should be erased professionally and in line with legal requirements. Many companies lack not only the necessary expertise but also the resources to do this. You can rest easy if you have tasked the right IT service provider with erasing your data and remarketing your equipment.
Contact us!
Feel free to contact us in case of questions!
Lukas Wojoczek
Functional Teamleader DWP / Senior Technical Sales
- CHG-MERIDIAN AG
- Franz-Beer-Str. 111
- 88250 Weingarten
- +49 7515 03 124
- +49 151 580 408 41
- lukas.wojoczek@chg-meridian.com



